Sign in
Sorry, we were unable to sign you in.
Please check your email address and password.
Please check your email address and password.
Navigation |
Types of FirewallTypes of Firewall
Enterprise Security Architecture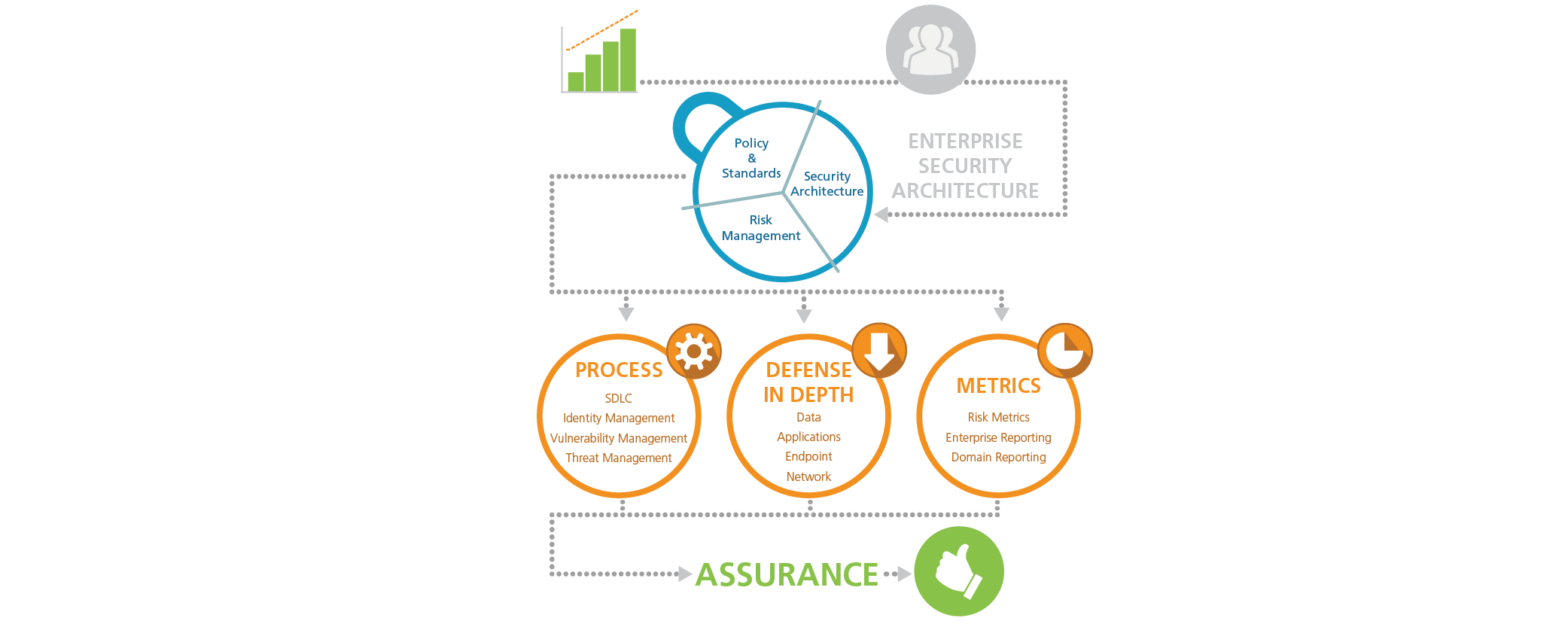 To find out more information on this topic and more, visit our section on Network Security |